The access control system is a security security system that is used in modern commercial buildings, communities, schools, and enterprises. The access control system is a modern security management system that integrates the automatic identification technology of microcomputers with modern security management measures. The access control system is used more in our daily life work, but how much do you know about the installation of the access control system? The following small series will share with you the installation and troubleshooting of the access control system.
Access control system installation
Access control system installation 1: equipment installation
1, front-end equipment
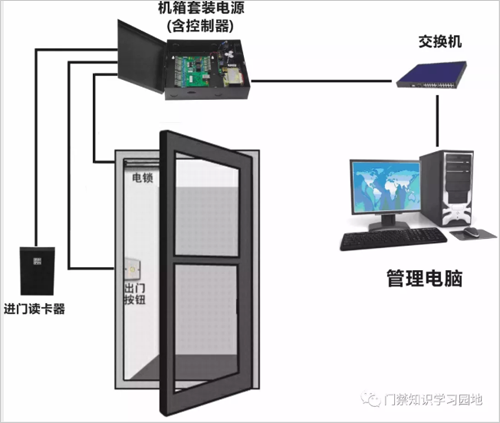
A. Install the card reader at the entrance. Do not approach or touch high frequency or strong magnetic fields (such as heavy-duty motors, monitors, etc.) within the sensing range of the reader, and cooperate with the grounding method of the control box.
B. Install the exit button at the exit door.
C. The electromagnetic lock is installed on the upper edge of the door and the door frame.
D. To ensure safety and aesthetics, the controller and power box can be installed in the field or installed in a weak electric well. The advantage of on-site installation of the controller is to save the use of wire. The controller is installed in the weak electric well to facilitate future maintenance of the system and the safety of the system. The controller box can also be installed above the card reader and close to the electromagnetic lock. The specific situation can be selected according to the customer's installation method.
2, the central control room equipment
A. The control panel and keyboard are mounted on the facade wall or placed on the workbench.
B. The alarm device is placed at a position where the alarm effect is good.
C. Due to the special nature of the access control system, it is required to supply power to the system. It is recommended to use UPS power supply to centrally supply power to the access control system.
Access control system installation 2: equipment debugging
1. After the system is installed, first access the signal of the access control card reader to the host, and then separately detect the situation of the access control card reader, whether there is any false negative or false alarm. After the road detection is no problem, it is connected to another road. In this way, each road is tested separately, and all the lines are connected after the confirmation is correct.
2. The management personnel can separately authorize according to the authority of the user. For example, some personnel can enter and exit any place at any time. The ordinary personnel can only enter and leave the authorization scope within the authorization time by the authorization card. When all access points are normally turned on and turned on illegally, check if the control center computer has a record.
3. If the central computer cannot be connected to the controller due to malfunction or other reasons, can the controller independently record the relevant information of the controlled door point. When the central computer is connected, can all information be automatically uploaded, and whether the information record can be guaranteed intact? Sex.
4, do a good job of debugging records.
5. Finally fill in the completion report.
Access control system installation three: pipeline installation
1. Installation and wiring should comply with national regulations; electrical installation engineering construction and acceptance specifications; and relevant national regulations and regulations. Threading in the pipe or in the trunking shall be carried out after the construction plastering and ground works. The water and debris in the pipe or in the trunk should be removed before threading. Lines of different systems, different voltage levels, and different current types should not be worn in the same tube or in the same slot of the slot. The wire shall be inside the pipe or in the trunking and shall not have joints or kinks. The connectors of the wires shall be soldered in the junction box or connected by terminals. Small-section system connections can be spliced, the number of twisted turns should be more than five inches, then tinned, wrapped with insulating tape. The pipeline shall pass the deformation joints of the building (including settlement joints, expansion joints, anti-seismic joints, etc.), and compensation measures shall be taken. The conductors shall be fixed across the deformation joints with sufficient margin. Terminals in the terminal box should be crimped or terminal strips with solder joints, and the terminals should have a label.
2. The access controller should be installed firmly, not tilted, and should have obvious signs.
Installed on a lightweight partition wall, reinforcement measures should be taken. Introduce the cable or wire of the access controller, the wiring should be neat and avoid crossover, and the part of the cable core wire and the wire to be fixed should be fixed, and the drawing should not be faded; the terminal block and each terminal, wiring No more than two; the cable core and the wire should be left with a margin of not less than 20cm; the wire should be bundled into bundles; after the wire lead-through wire is threaded, it should be sealed at the inlet pipe.
3. The main power inlet of the access controller should be directly connected to the power supply. It is strictly forbidden to use the power plug. The main power supply should have obvious signs; the grounding of the access controller is firm and has obvious signs.
4. The routing and specifications of the monitoring indoor grounding busbar should meet the design requirements. The following rules should be met during construction:
The surface of the grounding busbar should be complete, no obvious damage and residual flux slag, copper busbar light, slippery and burr-free, and the insulation layer must not have aging cracks;
The grounding busbar shall be placed in the center of the trough or cable walkway and fixed on the outside of the trough. The busbar shall be flat and shall not be skewed or bent.
The connection between the busbar and the rack or the roof should be firm; the copper busbar on the cable walkway can be fixed by screws, and the copper stranded busbar on the cable walkway should be tied to the crossbar; the system lightning protection grounding installation should be Construction in strict accordance with design requirements. Grounding installation should be carried out simultaneously with civil construction.
Four exclusions for access control system failure
Method one, software test method
1. Detection method: Start the management software, enter the main console to select the door, click the detection controller, the software operation information will prompt the relevant fault, then it can be processed according to relevant information.
2, real-time monitoring method: the main console → real-time monitoring, real-time monitoring corresponding to the corresponding card indicator to facilitate the detection of the card does not open the door failure.
3, search .net method: basic settings → controller → search .net, help to find the communication fault of the TCP / IP controller corresponding to the communication indicator helps to find communication faults. (Note: Please turn off the firewall!)
Method 2, hardware indicator method
1. When power is on, we can see the power indicator POWER, and the CPU indicator flashes to determine if the controller is working.
2. When swiping the card, we can look at the card light to determine if there is any card data transfer to the controller.
3. Press the exit button, we can see the relay indicator, whether it is ringing or not, to determine whether the controller relay output is normal.
4. When watching the TX and RX lights during the communication operation, the TCP controller Rx (Link) light is always on and the wiring is basically no problem. The Tx light flashes to indicate that communication is in progress.
5. The err light flashes to indicate that the controller has failed, and detailed information is obtained in the software test.
6. The network controller can also look at the power indicator. When the ping is on, the Rj45 port indicator flashes alternately.
Method three, replacement exclusion method
1, equipment replacement method: This can only be referenced, can not be completely determined, because if it is caused by an environment or factors will not be immediately expressed, just like a person's chronic disease has an incubation period, the passage of time will also cause problems Appears, if you replace the suspected problematic equipment, there is no problem with separate detection, this may be environmental interference problems such as wiring, and you should actively continue to find the source of the fault.
2, computer replacement method: can determine whether it is the customer's computer or operating system environment, virus problems, serial output or settings are wrong.
3, database, software replacement method: such as the failure to extract records or upload settings, report failure, etc., you can use another brand new database or software to determine the scope of the problem.
Method 4, separation and exclusion
1. With the access controller as the core, many externally controlled devices can be connected, and the quality parameters of the external devices are uneven. Compatible with interference, the resulting phenomenon is also strange, such as controller restart, ERR light Blinking, the door is abnormally open and closed, you can separate the external equipment to see if it is normal, then load each external device one by one, and load a test to see what is loaded causing this fault, such as three stick gates, gates, bells Elevators, automatic doors, and various alarm devices connected to the expansion board may be sources of interference. The solution is to install weak current isolators.
2. The TCP controller uses the conventional method to not connect to the network in the customer network. It can independently test the OK from the customer network and use the independent switch to test OK. Seek the support of the network management of the party to see if other network authentication restrictions are enabled.
Metal Cans,Metal Can With Lid,Aluminum Can,Aluminium Tin Can
Jiangyin keyi packing Material Co.,Ltd , https://www.keyipacking.com